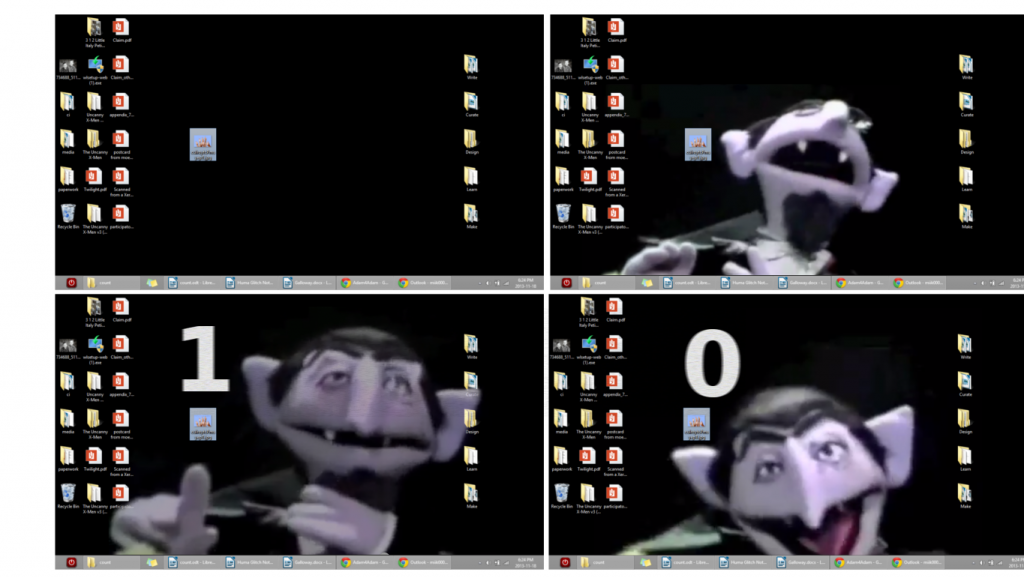
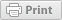
Boot Camp: Count von Counterprotocol
“We can count, but we are rapidly forgetting how to say what is worth counting and why.”
-Joseph Weizenbaum (16)
Sesame Street’s Count von Count—a Bela Lugosi-style Transylvanian vampire plutocrat muppet of ostensible Romani origin with obsessive compulsive tendencies—holds a worldview which is essentially quantitative.1 Like the wielder of a golden hammer, to whom everything looks like a nail, the Count’s déformation professionnelle limits his outlook to those things which are countable.2 This myopia is cause for concern in instances where his own emotions subside into the cold logic of numerical abstraction; where his taste for counting comes at odds with the sensual body (as portrayed with Cookie Monster, or on a picnic); where he thwarts the creative endeavours of others; where he is faced with the impossible task of enumerating chaos; or where his love of numbers trumps the desires of a significant other.
This Boot-Camp approaches a widespread diagnosis of this Count Syndrome—a particular worldview shaped by the proliferation of numeric abstraction—afflicting those of us affected by digital culture. It further proposes a treatment in the form of a computer virus.
Count von Counterprotocol is a (theoretical) program designed to render explicit the numerical, binary coding that makes up digital media. The malware furtively infiltrates one’s personal computer but does not corrupt or alter any component of the machine. Rather, the virus commands that any and every file opened on the computer be executed as a video of the Count reading aloud each of the file’s bits (ones and zeroes) in sequence. As even a tiny file of 1kb contains over 8000 bits, the virus impels a tedious, protracted reading of digital media that imparts a decidedly limited view of one’s files along their numerical lines. The process insists against interpreting or reading files via the sanctioned protocols that make them comprehensible to human subjects. In ‘fucking up’ these protocols, the program obliges a raw purview of the underlying codes that allow for digital systems to control and order flows of information.
In 1976 the renowned humanist technologist Joseph Weizenbaum put forth an argument now familiar to critics of digital culture. He critiqued the current state of science and technology as mounting from a “passion for certainty” and “quest for control” (126). This concern for unambiguous and governable systems, aside from being consciously developed for technical instruments, stems from a set of unconscious methodological and ideological biases that political theorist Isaiah Berlin recognizes as a heritage of the platonic ideal, in which “all genuine questions must have one true answer and one only, all the rest being necessarily errors” (3). This dominant, binary outlook permits only claims that abide by the law of the excluded middle (true or false) and exclusive disjunctions (either / or operands). If this worldview saw Galileo affirm the centrality of mathematics—that ‘language of the universe’— in the seventeenth century, the same worldview carried the “influence of mathematical logic” into modern cybernetics (Wiener 12).
A harbinger of the digital computer, the field of cybernetics aimed in the twentieth century toward the mechanization of symbolic reasoning. Through feedback, systems analyses, and techniques of control, cybernetics developed a certain quantitative outlook of ‘systems’ as diverse as telephone networks, ecosystems, and human bodies. This mechanized, measured perspective has deeply infected metaphysical understandings of reality, as a dominant force that Jaron Lanier calls Cybernetic Totalism. Here, the self is to be understood as a mere information processor, or the natural environment as a plain set of measurable, biological processes, in what entails a considerably dumbed-down worldview that edits-out unmeasurable complexities and unknowables. This simplified, limited technological outlook based on the centrality of certainty, neglects what Weizenbaum meant when he proclaimed that “there is an outer darkness” (127)—a deep and unapproachable uncertainty that is, as Bifo Berardi and Alessandro Sarti have written, an “intrinsic ontological feature of natural reality” (60).
Such vast unknowables and unthinkables tend not to find representation in computer software, probably for reasons of practical utility (I wouldn’t want MS Word to constantly remind me of the fundamental mysteries and paradoxes of the universe). However, this lack of transparency in digital systems—heavily structured control-machines—is coloured by these larger ideological imperatives toward certainty and order. Based ultimately upon binary systems (what Kittler reduces to its material “voltage difference”3) digital computers necessitate a controlled engagement along binaries: either on, or off. As critic Jan Verwoert has observed, “it is a system based on the constant repetition of either/or choices” (18). In the streamlined efficiency of its interfaces is a “tendency,” as Alexander Galloway explains, “for software to priviledge surface over source” (291). And in this privileging does software hide the biased protocols of its control systems, in what Wendy Chun calls “software’s uncanny paralleling of ideology” (22).
Galloway has developed a sophisticated study of protocological ideology within digital culture.4 At its most basic form, these are standardized technical protocols that sanction access on the Internet, as seen in the functioning of informational systems like TCP/IP, DNS, UDP, and HTTP.5 These systems enable interaction between entities online, but also restrict how and what type of information is shared. Such highly-regulated control structures often go unseen in engagements with the Net—commonly thought of as an open-access, horizontal field devoid of hierarchical powers. Galloway here provides a critical lens with which to see the general functioning of power in digital networks. More than just rules and regulations for online activity, protocol represents ideological forces that underlie these networks.
Significantly, Galloway’s framework also accounts for forces of political resistance against protocols.Here, through what he terms counterprotocol, critical rifts can be torn into both the technological and, hence, ideological structures of digital systems. Protocols, then, allow for their own undoing: not merely a hegemonic system, “protocol is synonymous with possibility” (244). Counterprotocol practices are modes of resistance within-but-against protocological structures. They are practices that enable the penetration of a system in order to exploit it. Not the mere wrench-in-the-machine of neo-Luddism, counterprotocological activity infiltrates and works with ‘the machine’ in order to undermine and leverage its power.
It is this disruption that the Count von Counterprotocol virus aims toward. It renders visible (though absurdly and incomprehensibly) the basic structures of computation, and the protocols that shape ideological engagement with them. The virus compels a raw look at a file’s underlying material structure – foregoing the computer’s designs toward communicating information, in favour of representing its more ‘pure’ data. Like Moretti’s distant reading, it is limited to the degree that “it provides data, not interpretation” (72). In rendering mere binary code, though, it attempts to make visible what sociologist Manuel Castells has called the “unseen logic of the meta-network” (508), and consorts with Geert Lovink’s call to “revolt against the mathematical shapes of networks” (23). It attempts to open a critical fissure through which the fixed definitions and impenetrable logic of the computer may become questionable and uncertain.
Works Cited:
Berardi, Franco Bifo and Alessandro Sarti. RUN Morphogenesis. Kassel: Documenta und Museum Fridericianum, 2012.
Berlin, Isaiah. “On the Pursuit of the Ideal,” The New York Review of Books. 35.4. 1988.
Castells, Manuel. The Rise of the Network Society. Malden, MA: Blackwell, 2000.
Chun, Wendy Hui Kyong. Control and Freedom: Power and Paranoia in the Age of Fiber Optics. Cambridge, MA: MIT, 2006.
Galloway, Alexander. “Networks.” Critical Terms for Media Studies. W.J.T Mitchell and Mark Hansen, University of Chicago Press, 2010.
Lanier, Jaron. “ONE HALF A MANIFESTO.” Edge.org, 11 Nov. 2000. Web. 1 Nov. 2013. <http://www.edge.org/conversation/one-half-a-manifesto>.
Lovink, Geert. Networks Without a Cause: A Critique of Social Media. Cambridge, UK: Polity, 2011.
Moretti, Franco. Graphs, Maps, Trees: Abstract Models for a Literary History. London: Verso, 2005.
Verwoert, Jan. “Exhaustion an Exuberance.” Tell Me What You Want, What You Really, Really Want. Sternberg Press, 2010.
Weizenbaum, Joseph. Computer Power and Human Reason: From Judgement to Calculation. San Francisco: W.H. Freeman, 1976.
Wiener, Norbert. Cybernetics; Or, Control and Communication in the Animal and the Machine. New York: M.I.T., 1961.
Footnotes:
1I owe credit to the artist Adam Kaplan, who coined the concept of the Count Syndrome. adamkaplan.net
2Perhaps comparable to Weizenbaum’s “drunkard’s search syndrome” (130).<http://en.wiktionary.org/wiki/if_all_you_have_is_a_hammer,_everything_looks_like_a_nail>
3“All code operations (…) come down to absolutely local string manipulations and that is, I am afraid, to signifiers of voltage difference.” Kittler, Gramophone, Film, Typewriter (Stanford, CA: Stanford UP, 1999), 15.
4Permeating much of his work over the past decade, it has found its most thorough articulation in his 2004 publication: Alexander R. Galloway, Protocol: How Control Exists after Decentralization (Cambridge, MA: MIT), 2004.
5 Transmission Control Protocol (TCP), Internet Protocol (IP), Domain Name System (DNS), User Datagram Protocols (UDP), and Hypertext Transfer Protocol (HTTP) structure the dominant uses of the Internet.